
.png)
.png)


Frequently Asked Questions
The eIDAS regulation of the European Union, aims at creating a unified digital identity framework. The updated eIDAS 2 regulation introduces the European Digital Identity (EUDI) Wallet, a mobile app for secure digital identity management. The EUDI-Wallet allows users to store and use digital identities, access services across EU member states, and sign documents electronically.
The first version had challenges like complex architecture and restricted private sector use, which eIDAS 2 aims to address by expanding electronic trust services and fostering digital signature adoption. The EUDI-Wallet, central to eIDAS 2.0, enhances cross-border interoperability, user privacy, and data protection, aiming to provide a seamless and trustworthy digital environment in the EU, covering various sectors like healthcare and financial services.
- OpenID4VC, which includes OpenID4VCI (OpenID for Verifiable Credential Issuance) and OpenID4VP (OpenID for Verifiable Presentations).
- SD-JWT-based Verifiable Credentials with JSON payloads (SD-JWT VC).
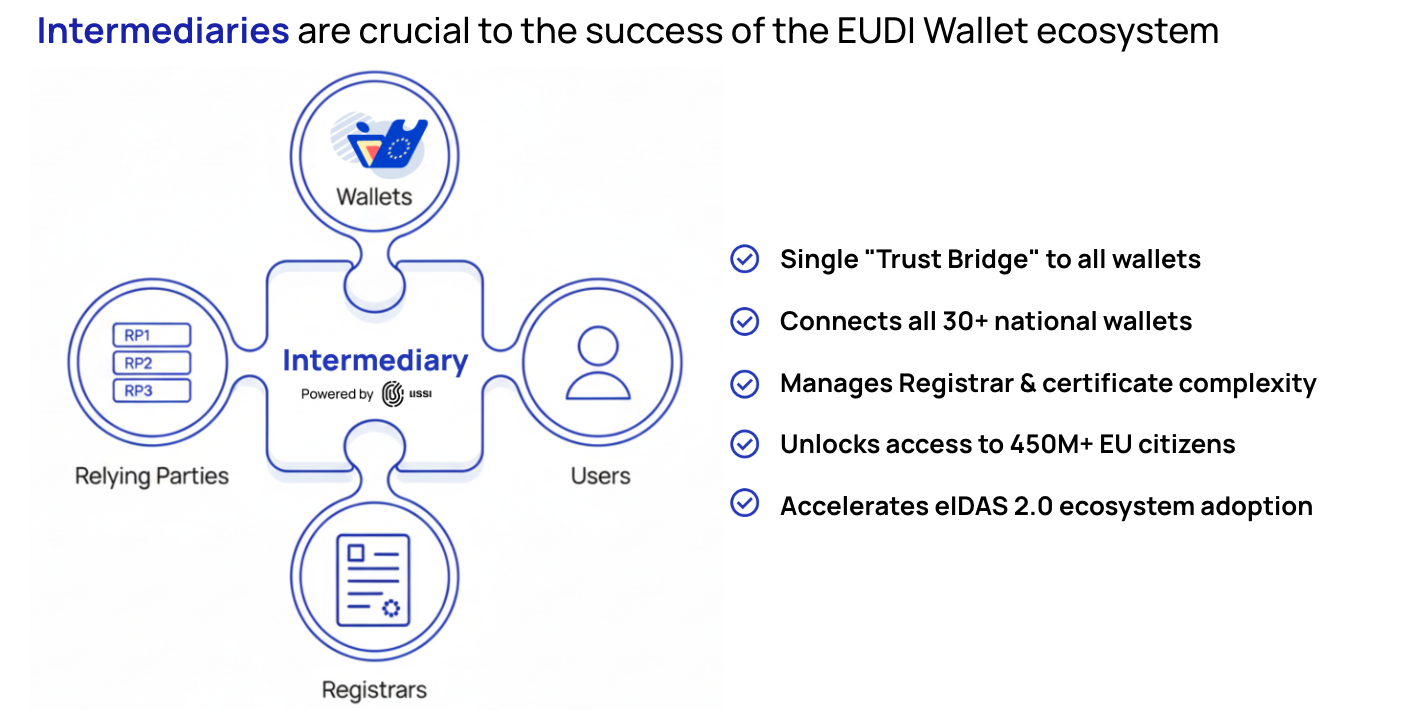
The Lissi ID-Wallet is set to align with the technical standards defined for EUDI-Wallets in the architecture reference framework, showing a proactive step towards adherence to the evolving digital identity framework in the EU. However, the path towards becoming a certified EUDI-Wallet is not fully clear at the moment due to the yet to be defined regulatory requirements and the regulatory overhead associated with the certification of an EUDI-Wallet. The European member states have the autonomy to decide whether they wish to provide an EUDI-Wallet themselves or open up the market for private participants like the Lissi Wallet. There's potential for the Lissi Wallet to pursue certification to become an official EUDI-Wallet provider in member states such as Germany. However, as of now, the lack of comprehensive information regarding the regulatory landscape and the certification process makes it challenging to ascertain the likelihood or the timeline within which the Lissi Wallet might achieve the status of an EUDI-Wallet. Hence, while the intention and initial steps towards alignment with EUDI-Wallet standards are apparent, the definitive trajectory of the Lissi Wallet becoming an EUDI-Wallet remains contingent on forthcoming regulatory clarifications and decisions by individual EU member states.


.png)
