Introduction: The Integration Challenge
The eIDAS 2.0 regulation is no longer a distant concept; it is a fixed deadline. By 2026, all EU Member States are required to provide their citizens with a European Digital Identity Wallet (EUDIW). Just one year later, by December 2027, organizations in regulated sectors -including banking, financial services, and telecommunications - will be legally obligated to accept the EUDIW for processes like Strong Customer Authentication (SCA) and secure identification.
However, connecting to this new ecosystem is not a simple "plug-and-play" update. For a single organization, direct integration is a massive undertaking. The challenge isn't just one wallet; it's a "pyramid of complexity" built from multiple, interconnected layers:
- Wallet Fragmentation: Integrating and maintaining connections with 30+ unique national and private wallets.
- Protocol Complexity: Implementing and constantly updating evolving protocols like OpenID4VP, OpenID4VCI, and SD-JWT.
- Trust Infrastructure: Managing a complex web of national trust lists, certificate lifecycles, and robust revocation checks.
- Regulatory Dynamics: Ensuring perpetual compliance with new Implementing Acts and evolving security standards.
For most Relying Parties, building and maintaining their own EUDI Wallet Connector to handle this complexity makes little business sense and represents a significant strategic drain on resources. This market structure logically demands a specialized infrastructure layer to abstract away the complexity and manage trust at scale. A role the regulatory framework defines as the Intermediary.
What is an EUDI Wallet Intermediary?
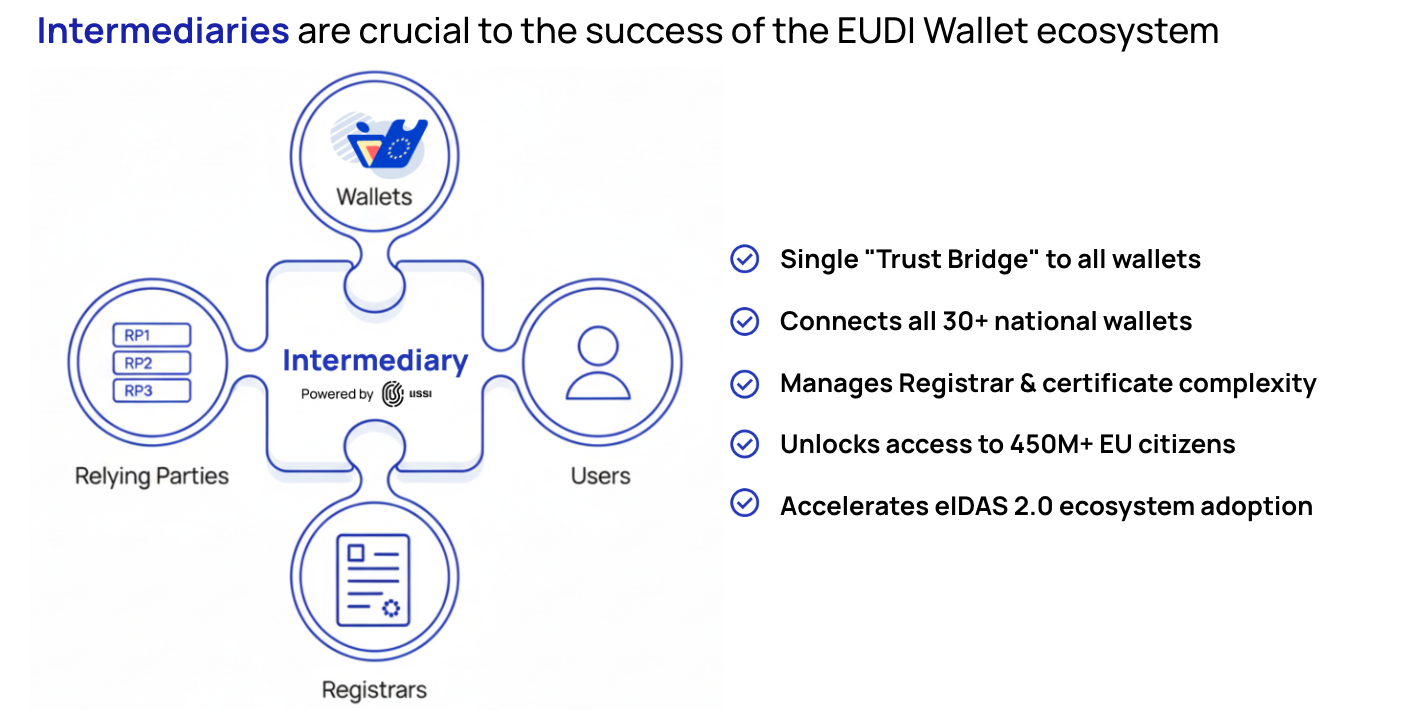
At its core, the Intermediary is a defined role within the eIDAS 2.0 regulatory framework designed to solve the ecosystem's fragmentation.
The Architecture and Reference Framework (ARF) provides a clear definition:
"So-called intermediaries form a special class of Relying Party. Article 5b (10) of the [European Digital Identity Regulation] states "Intermediaries acting on behalf of relying parties shall be deemed to be relying parties and shall not store data about the content of the transaction". Such an intermediary is a party that offers services to Relying Parties to, on their behalf, connect to Wallet Units and request the User attributes that these Relying Parties need."
In simple terms, an Intermediary is a "trust bridge". It's a specialized, regulated entity that manages the intricate technical, legal, and operational complexity of wallet interactions, offering this connection as a streamlined service to other organizations.
Think of them as the "trust hubs" or "aggregators" of the new identity ecosystem. Much like a payment network (like Visa or Mastercard) connects thousands of banks to millions of merchants, an Intermediary connects thousands of Relying Parties to the 30+ different EUDI Wallets. They absorb the complexity so their clients don't have to.
The 'Greenfield' Opportunity: A New, Mandated Market
This new regulatory framework isn't just a compliance burden; it's a time-sensitive 'gold rush' . eIDAS 2.0 is a rare market-creation event, establishing a brand-new, legally mandated €1B+ ecosystem from scratch. For organizations positioned to become Intermediaries, this represents a definitive "greenfield" opportunity to create new, high-margin revenue streams. The business model is uniquely powerful because the demand is not speculative. It's guaranteed by law. Your target customers (banks, telcos, insurers, and other Relying Parties) are legally obligated to find a solution by the 2027 deadline. Your job is not to create a market, but to capture existing, mandated demand.
This is a race. The first Intermediaries to offer a robust, compliant, and easy-to-use platform will capture the market. Time-to-market will be the single most critical factor for success
Organizations with existing trust relationships, technical infrastructure, and large customer networks are in a uniquely powerful position to win.
- Qualified Trust Service Providers (QTSPs): As a QTSP, you are already a cornerstone of the eIDAS framework. This is a once-in-a-generation opportunity to evolve from a provider of secure signatures into the central source for all verifiable digital attributes in your national economy. You are legally positioned as the exclusive issuer of high-trust Qualified Electronic Attestations of Attributes (QEAAs), and by acting as an Intermediary, you can bundle this with high-demand Person Identification Data (PID) verification for KYC, creating a comprehensive, high-margin portfolio.
- Identity Verification (IDV) Platforms: You are perfectly positioned to leverage your established brand and deep client integrations to lead the market's transition away from costly, high-friction VideoIdent. Your opportunity is twofold: first, to provide a superior KYC solution using PID verification that is massively faster, cheaper, and more secure , and second, to expand your business model from one-off verification into an ongoing trust platform by issuing and verifying credentials on behalf of your enterprise clients .
- Payment Providers & Hubs: This group—including issuers, acquirers, payment service providers, and other financial hubs—is central to the security and efficiency of the digital economy . You are uniquely positioned to leverage the EUDI Wallet to reduce fraud and streamline the customer experience. As an Intermediary, your core opportunity is to deliver a superior Strong Customer Authentication (SCA) solution for online payments . This can be bundled with other high-value services, such as issuing dedicated payment credentials (like tokenized IBANs) , streamlining merchant onboarding with PID-based KYC , and creating innovative new "payment + identity" transactions.
- Public Sector Service Providers: Your organization is the engine of public sector digital transformation. You are the natural choice to act as the central Intermediary hub for your entire network of municipalities, government agencies, and public bodies, ensuring they can meet eIDAS 2.0 requirements. Your mandate is to enable the issuance of Public Electronic Attestations (PubEAAs) like residency confirmations , manage the secure connections to definitive "authentic sources", and enable high-assurance authentication for all citizen portals using PID.
By becoming the essential link, you not only open new revenue streams but also secure the customer relationship. You become the embedded, indispensable "trust layer" for your clients, creating a powerful position from which you can add future value-added services.
The Key Decision: Host a Connector or Use an Intermediary?
Before an organization can connect to the EUDI Wallet ecosystem, it faces a critical strategic choice. This isn't just a technical question; it's a decision about control, cost, and compliance.
The key differentiator is "who hosts the application."
Option 1: Use an Intermediary Service: Most organizations - especially small to medium-sized enterprises (SMEs), regional businesses, and Relying Parties without large, dedicated compliance departments - will not have the resources or technical expertise to manage their own connection. Their best strategy is to "buy" access as a service from a trusted Intermediary.
Option 2: Host Your Own Wallet Connector: For major, regulated organizations, this is the clear strategic choice. Large banks, telecommunication providers, insurance companies, and major public sector bodies have the transaction volume and the strict data-sovereignty requirements that justify managing their own infrastructure. This path involves licensing a production-ready "EUDI Wallet adapter," like the Lissi Connector, and running it within your own on-premise or private cloud environment.
This table compares the two primary models for a Relying Party:
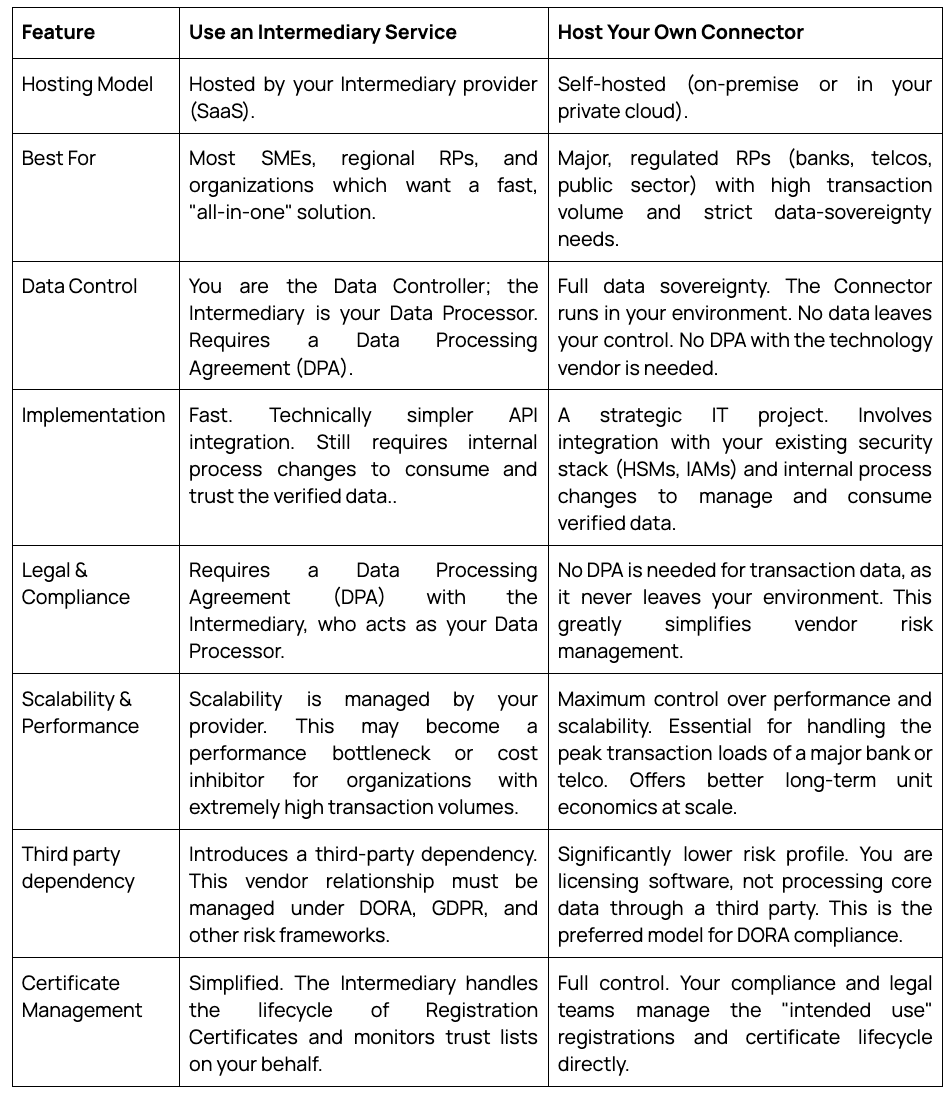
Regardless of the path chosen, one fact is clear: very few organizations will attempt to build this core technology themselves. The complexity, cost, and perpetual maintenance burden are too high. They will either buy access from an Intermediary, or they will buy a Connector like an Intermediary. For those organizations looking to become an Intermediary, it's essential to understand the true scope of the challenge.
The Core Challenges of the Intermediary Role
Becoming an Intermediary is a powerful move, but it is not a simple undertaking. The role carries significant legal, operational, and technical responsibilities. Any organization seeking to become an Intermediary must be prepared to solve three core challenges.
1. The Legal "No-Storage" Mandate
The most critical requirement is a legal one. The eIDAS 2.0 regulation explicitly states that Intermediaries "shall be deemed to be relying parties and shall not store data about the content of the transaction". This "no-storage" mandate is absolute and shapes the entire architecture.
- Stateless Processing: An Intermediary must not persist any personal data, verifiable credentials, or transaction content.
- Immediate Deletion: Data obtained from the wallet, such as PIDs or attributes, must be deleted "completely and immediately" after being forwarded to the end-Relying Party. This also applies to metadata like IP addresses.
- Strict Purpose: Data is processed only for the purpose of forwarding requests and handling protocol complexity.
This requires an architecture built from the ground up for stateless, stateless processing, where audit logs are content-free by design.
2. The Operational Challenge: Certificate Lifecycle Management
This is the central operational complexity of the Intermediary role. To ensure transparency for the end-user, the Intermediary must manage a sophisticated portfolio of cryptographic certificates. Every transaction involves two distinct types of certificates:
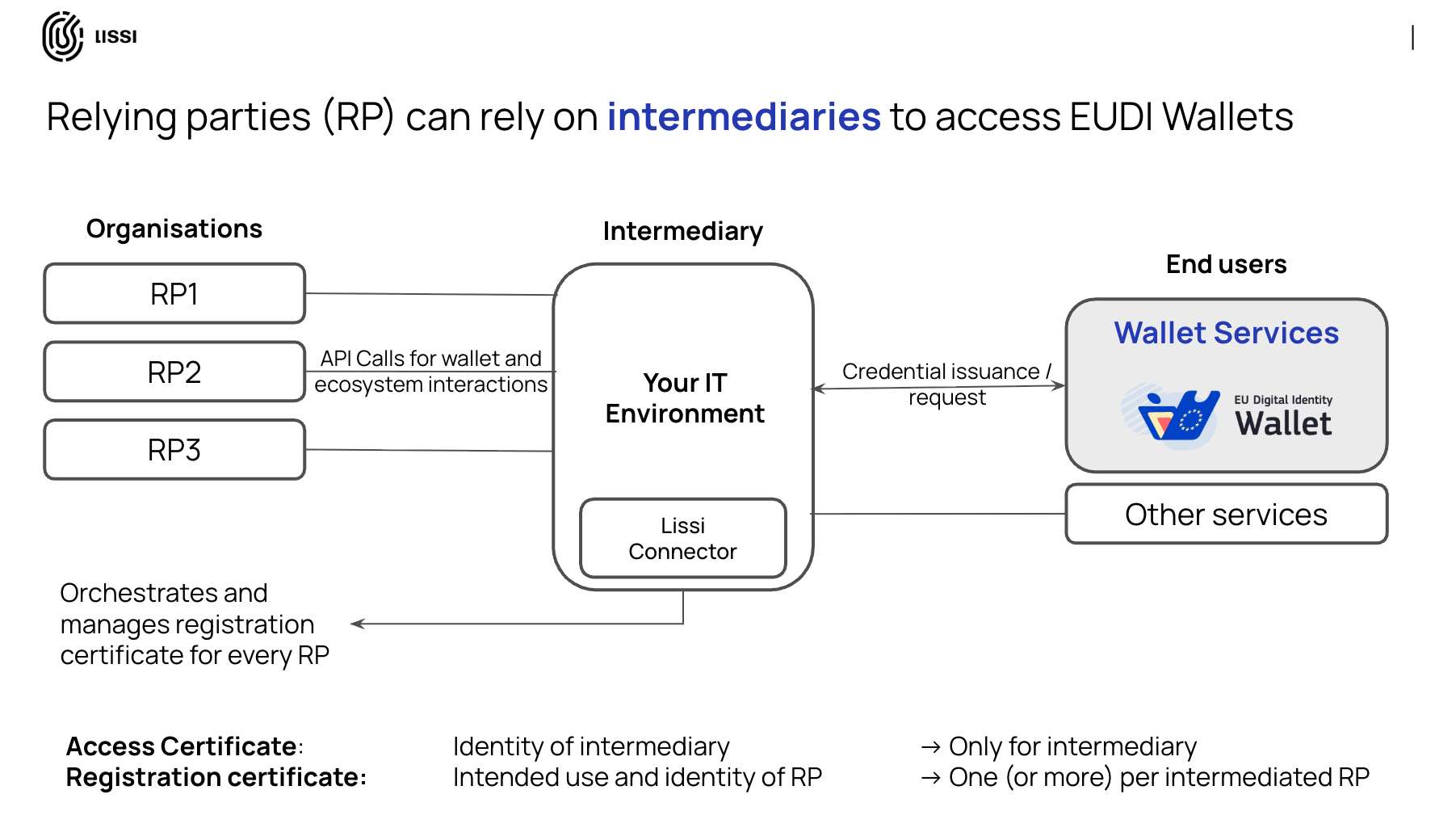
1. The Access Certificate (Verifying 'Who' You Are): This is the Intermediary's own "digital passport". The Intermediary must register itself as a Relying Party to obtain its own Access Certificate, which authenticates its own identity in every transaction.
2. The Registration Certificate (Verifying 'Why' You Ask): This certificate answers the user's key question: "Why is this organization asking for my data?". The Intermediary is responsible for separately registering each of its clients (the "end-Relying Parties") and each of their specific "intended uses" (e.g., "KYC for bank account" or "SCA for payment").
For every single transaction, the Intermediary must present both its own Access Certificate and the specific Registration Certificate that belongs to the end-RP it is serving for that exact use case.
The EUDI Wallet is designed to display the identities of both the Intermediary and the end-RP, ensuring complete transparency for the user. This means the Intermediary is operationally responsible for securely managing a complex and massive portfolio of Registration Certificates for all its clients and their diverse use cases.
3. The Perpetual Technical Burden
The Intermediary's third challenge is absorbing the entire technical complexity of a fragmented and evolving ecosystem. This is not a one-time build; it is a permanent maintenance commitment. This burden includes:
- Wallet Interoperability: Building and testing point-to-point integrations for over 30+ national and private EUDI Wallets, each with its own quirks for interoperability.
- Protocol Churn: Implementing and constantly adapting to multiple, evolving standards, such as OpenID4VP, OpenID4VCI, SD-JWT VC, and ISO 18013-5/-7.
- Trust Management: Integrating and continuously managing multiple national trusted lists, complex PKI certificate lifecycles, and robust, real-time revocation services (e.g., PID Provider lists, RP Access Certificate Authorities).
- Ecosystem Evolution: Endlessly monitoring and adapting to new regulations, security standards, and technical updates as the ecosystem matures.
The "Build vs. Buy" Accelerator
For any organization looking to become an Intermediary, this leaves one final, critical decision: do you build this complex engine yourself, or do you buy it from a specialist?
The "Build" Path: A High-Risk, Multi-Year Endeavor
Attempting to build an Intermediary platform from scratch in 2026 is a 7-figure, multi-year commitment. The few organizations that are successfully pursuing an in-house build have already invested years of research and development, spent millions on engineering, and actively participated in foundational ecosystem projects like the EU's Large Scale Pilots.
For any organization that has not already made this deep, long-term investment, starting an in-house build now is not just complex and costly; it guarantees a delayed market entry. The market is starting in 2026. Your platform might be ready at some point during 2027. By then, the most valuable Relying Parties will have already chosen their Intermediary partners, and you will be left competing for the scraps.
The "Buy" Path: The Time-to-Market Accelerator
The strategic alternative is to license a production-ready engine from a specialized vendor. This approach accelerates your time-to-market from 18+ months to a matter of months, allowing you to capture the market as it opens. Instead of diverting your best engineers to build and maintain complex protocol plumbing, you can concentrate on your go-to-market strategy, strengthening customer relationships, and designing compelling, value-added services. This model gives you the flexibility to bundle best-in-class solutions. Ultimately, this approach lets you focus on what you do best: selling your services and managing your clients, not managing a fragmented, ever-changing technical backend.
The Solution: The Lissi Connector as Your Intermediary Engine
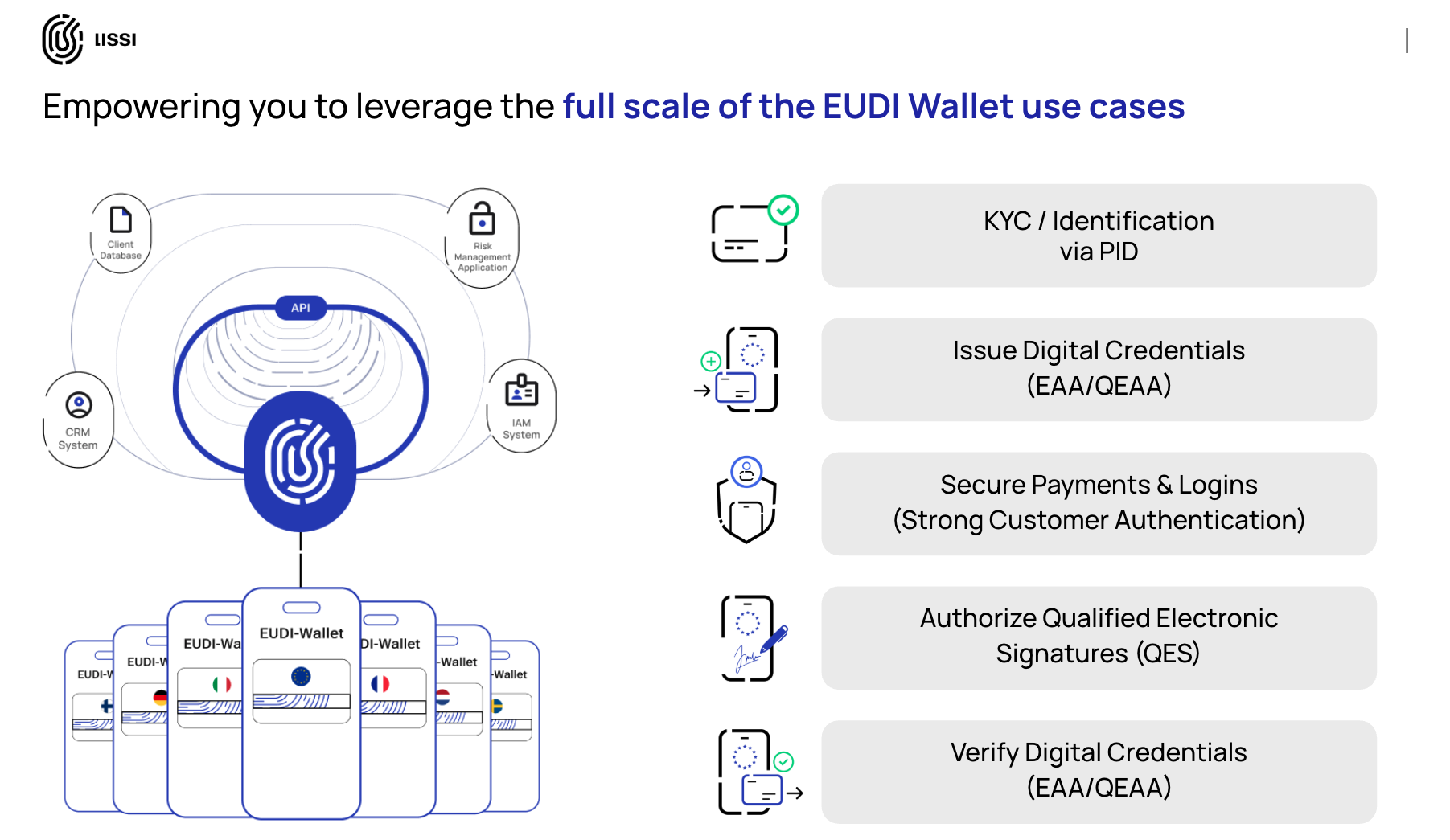
Lissi is not an Intermediary. We empower you to become one. We provide the core "engine" - the Lissi EUDI-WalletConnector - as a self-hosted, production-ready software component designed specifically for your Intermediary business model. It handles the underlying technical, security, and compliance complexity, allowing you to focus on your clients and your service.
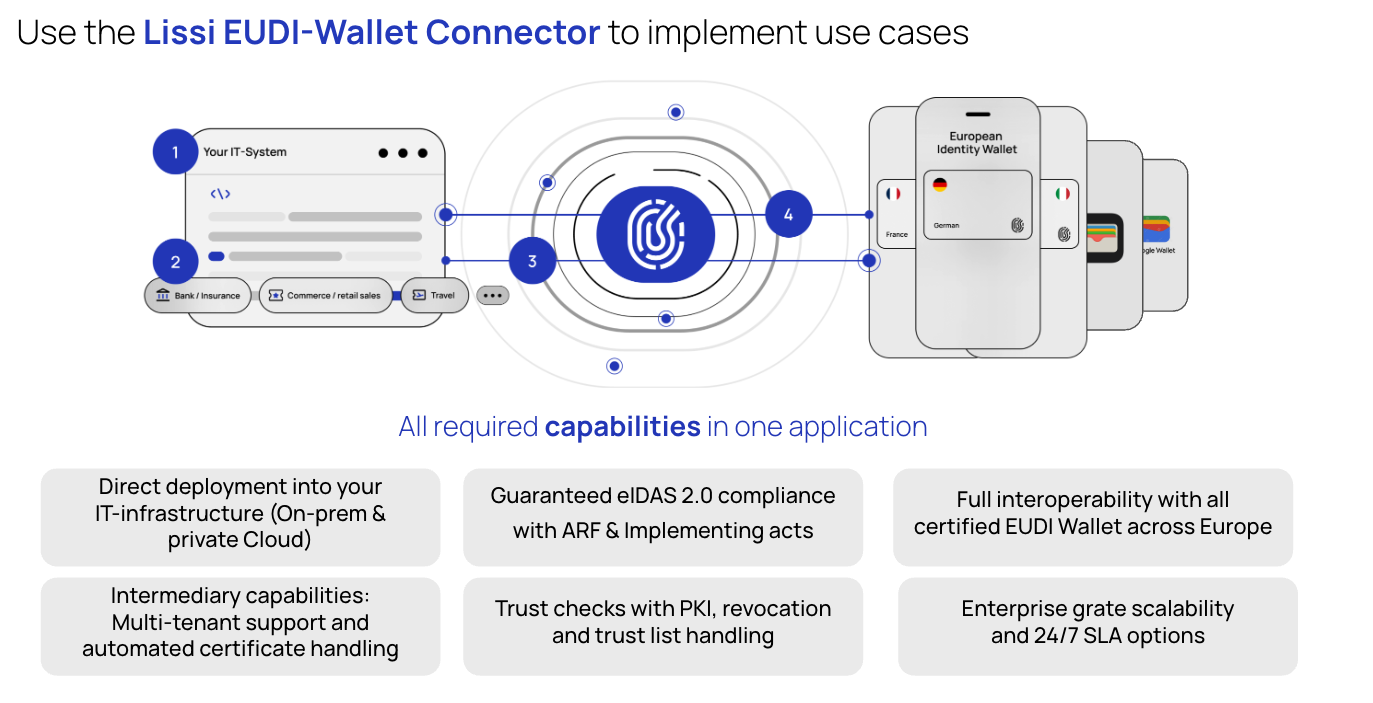
Here is why Lissi is the go-to partner for Intermediaries:
- On-Premise & White-Label by Design: We provide the Connector as a containerized software package (a Docker image) to run entirely within your own environment. This gives you 100% data sovereignty and control, allowing you to sell a true white-label service. Critically, because we never process end-user data, no complex Data Processing Agreement (DPA) is required between our companies.
- Multi-Tenant Architecture: Our platform is purpose-built for the Intermediary "one-to-many" business model. It is designed to securely manage all your downstream Relying Party clients in isolated, secure instances.
- Solves the Core Operational Hurdles: The Lissi Connector is engineered to solve the most difficult Intermediary challenges out-of-the-box. It provides the logic to manage the complex portfolio of Access and Registration Certificates and handles all protocol and wallet interoperability for you.
- Proven, Trusted & Battle-Tested: This is not a theoretical product. The Lissi Connector was co-developed with major European banks over 3+ years and is battle-tested in multiple EU Large Scale Pilots (like EWC and POTENTIAL).
- Deep Niche Expertise & Expert Guidance: We have worked for years with organizations on their path to becoming Intermediaries. We are active in the WE-Build Working Groups handling this exact topic and understand the "unknown unknowns" of this role. We don't just provide technology; we provide the expert guidance and strategic advisory to ensure your successful market entry.
We are proud to already empower a growing ecosystem of leading organizations on their path to becoming central Intermediaries in the EUDI Wallet market.



Conclusion: The Time to Act is Now
The EUDI Wallet Intermediary is the essential "trust bridge" that will make the eIDAS 2.0 ecosystem usable, secure, and scalable for millions of organizations. The opportunity to become a central pillar of this new digital economy is immense, but the window is closing. The market is forming now. The underlying standards are finalized, the regulatory deadlines are set, and large organizations are already beginning their procurement cycles to find a compliant solution. Time-to-market is the single most critical factor for success. Don't spend the next two years attempting a high-risk in-house build, only to arrive late. Focus on what you do best: managing your customers and capturing the market.
Don't build the plumbing. Buy the engine.






.png)