What you will learn in this guide:
A) The User's Perspective: Experience the complete user journey with our persona, Lara: From the initial wallet installation and account opening to everyday, cross-border interactions.
B) The Organization's Playbook: Get a detailed guide to the technical implementation of a seamless user experience: From configuring your display in the wallet and managing user flows to leveraging the forward-looking Digital Credential API.
C) The Ecosystem Outlook: Gain insight into the overarching challenges, such as credential discoverability (Discovery), the work of Europe's pioneers, and the necessary next steps to create a truly user-centric digital infrastructure for Europe.
With the finalization of the eIDAS 2.0 regulation, the European Digital Identity Wallet is set to become a cornerstone of Europe's digital economy. Its ultimate success, however, will not be measured by its technical specifications or regulatory compliance alone, but by a far more human factor: the quality of the user experience it delivers. We are at the cusp of a future where citizens can manage their entire digital lives with unprecedented ease, control, and security.
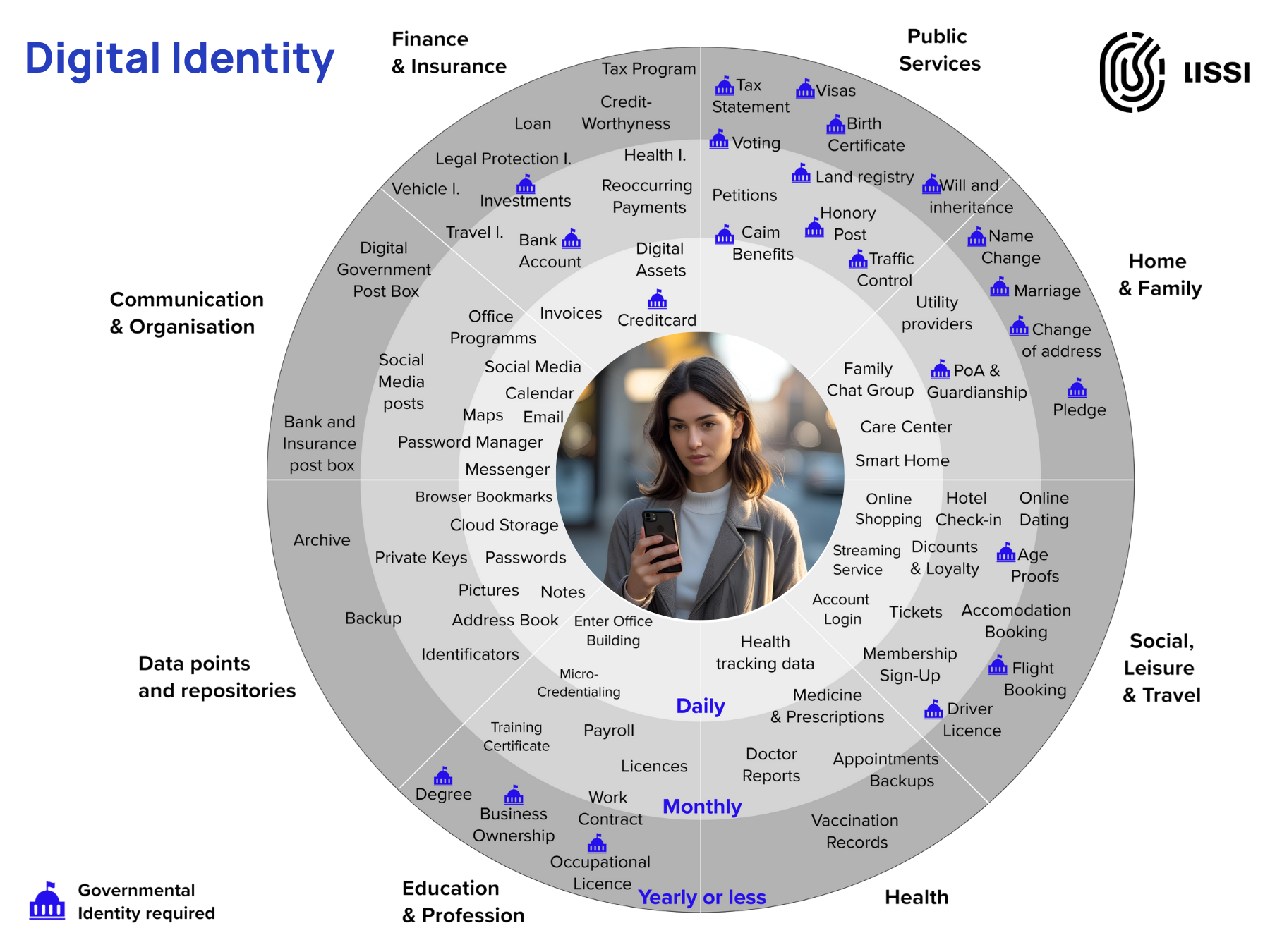
Imagine a person like Lara, a digitally native European citizen. Picture her enrolling at a university in another country, opening a bank account to receive a student loan, and signing a rental contract for her new apartment—all from her smartphone, in a single, seamless afternoon. This fluid, cross-border experience is the true promise of the EUDI Wallet. But this vision is not guaranteed; it is a promise entirely dependent on a frictionless, intuitive, and trustworthy user experience. This guide is a playbook for the organizations, innovators, and policymakers tasked with turning that promise into a reality.
1: The First Touchpoint: Wallet Choice, Person Identification Data, and Security
Lara's journey into the new era of digital identity begins not with a government form, but with a choice. As she explores the app store on her smartphone, she discovers that Germany, like many other EU countries, has opted for a dual approach: a government-provided EUDI Wallet alongside several certified applications from private companies. For Lara, this raises a critical question: how does she know which app to trust with her most sensitive data? The answer lies in a simple, powerful symbol: the EUDI Wallet Trust Mark. This official mark is a visual guarantee that a wallet has passed a rigorous certification process, ensuring it meets the high security and data protection standards mandated by the eIDAS 2.0 regulation. Organizations wanting to signal their acceptance of the wallet can use a general EUDI Wallet logo on their websites. Confident in her choice of a certified app, Lara begins the most crucial step: adding her official identity to the wallet.
This "digital birth" process, known as the issuance of the Person Identification Data (PID), is the bedrock of the wallet's security. The user experience here is paramount. Lara is guided through a familiar and secure procedure: using her existing German national ID card (Online-Ausweis) and her phone's NFC reader to transfer her verified identity data directly into the application. This process will vary across the European Union, as each Member State will leverage its own existing or newly created notified electronic identification (eID) schemes to issue the PID. However, the requirement is universal: the underlying eID scheme must meet the Level of Assurance 'High'. The specific data attributes that constitute a PID, such as name, date of birth, and address, are defined in detail within the Implementing Act (EU) 2024/2977, creating a standardized foundation for identity across the EU.
A core principle of user control is the user's responsibility for their digital credentials also referred to as electronic Attestation of Attributes (EAA). Therefore, a superior wallet UX must include robust, intuitive, and highly secure mechanisms for backup and recovery. This is not merely a feature but a fundamental requirement for building long-term user trust and ensuring the wallet can be reliably used for life's most important interactions. Alongside recovery, the eIDAS 2.0 regulation also mandates data portability, ensuring Lara has the freedom to switch between different certified wallet providers in the future without losing her valuable digital credentials. This reinforces the user-centric promise of the ecosystem: it is always the citizen, not the provider, who is in control.
2: The Cross-Border Challenge: Preparing for Life in Italy
Lara's journey as a European citizen is about to take a significant step as she plans her move from Germany to Italy to continue her studies. Before she can even think about packing, she faces a classic bureaucratic hurdle: she wants an Italian bank account to handle her tuition fees and future rent payments. Instead of anticipating a process filled with paperwork and in-person appointments, she downloads the app of a major Italian bank and discovers an option: "Open with EUDI Wallet." With a single tap, she is seamlessly guided to her wallet, authenticates with her biometrics, and is asked to consent to sharing her identity data (PID) with the bank. She agrees. Seconds later, she returns to the banking app with a confirmation message: her Italian bank account is open and ready to use.
This seamless experience is the core promise of the EUDI Wallet for Europe's Digital Single Market, but its success hinges on crucial details within the data itself. Lara's instant success was possible because her German Person Identification Data (PID) is a comprehensive dataset that includes her officially verified address. For the Italian bank, this meant they received a complete, state-verified identity package that instantly satisfied their strict Anti-Money Laundering (AML) and Know-Your-Customer (KYC) requirements.
.png)
However, this ideal user experience is not yet guaranteed for every citizen. The attribute set of a PID can differ from one member state to another. Had Lara's PID been from a country whose PID only contained a minimal dataset (e.g., name and date of birth but no address), the bank's automated process would have required an additional credential. The challenge for a seamless user experience then becomes: how does Lara easily find and provide that second credential, such as a certificate of residence? This is a question of "credential discovery," a crucial ecosystem function we will explore later in this guide.
For the Italian bank, accepting Lara's German wallet is not optional. The eIDAS 2.0 Regulation mandates that all EU banks must accept all certified EUDI Wallets for KYC, regardless of the Member State that certified them, creating a unified and competitive market for identity verification. For the bank trust is established technically and cryptographically through the Wallet Unit Attestation (WUA). This attestation is a digital proof that the bank is interacting with a genuine, certified wallet instance and not a fraudulent or uncertified application, ensuring the integrity of the entire transaction.
With the account successfully opened, the bank’s final onboarding step is to empower Lara to use it. The banking app immediately presents a new offer: "Add your new digital IBAN and credit card to your EUDI Wallet." Lara accepts, and the bank securely issues a new verifiable credential containing her account details directly into her wallet. This is more than just a digital copy of a plastic card; it is a high-trust, bank-issued attestation that she is the legitimate owner of this account and is authorized to transact with it. By issuing this credential, the bank is not just giving Lara her account details; it is equipping her for a new generation of secure digital commerce. This verifiable payment credential will be the foundation for all future EUDI Wallet-based Strong Customer Authentication flows, from online shopping to account information changes, creating a far superior user experience compared to legacy methods.
3: Life as a European Student: University, Housing & Delegation
Having successfully opened her Italian bank account, Lara now proceeds with the official enrollment at the Politecnico di Milano. This interaction showcases the power of the EUDI Wallet in breaking down digital borders for education and public services. On the university's portal, she again uses her wallet to present her German PID. The university system verifies her identity in real-time, and upon successful validation, immediately issues her official Digital Student ID directly into her wallet. She accepts, and the new credential appears, ready for use. This seamless issuance of a new, trusted credential is the logical outcome of a successful digital interaction, allowing Lara to build out her portfolio of verifiable attestations.
.png)
The power of these credentials becomes clear as she secures housing. The landlord sends her a digital rental contract to her tablet. Instead of printing and scanning, Lara clicks "Sign with EUDI Wallet," which displays a QR code on her tablet screen. She opens her wallet app on her phone and scans the QR-code. This initiates a cross-device process: her wallet receives a single, combined request to both verify her identity by presenting her PID and authorize the creation of a Qualified Electronic Signature (QES). After she approves with her biometrics, the signature is applied, and the document on her tablet is updated as legally signed. The implementation of this QES flow was defined and tested in the POTENTIAL Large-Scale Pilot, and Lissi has already implemented these specifications in both its API and wallet, to enable qualified trust service providers to implement the use case.
As Lara finalizes her move, her situation highlights a crucial area for the ecosystem's future development: what if her rental contract had required a co-signature from a guardian, or if she needed to authorize her parents to handle an administrative task on her behalf? This is the complex challenge of guardianship and delegation. While the EUDI Wallet excels at proving an individual's identity, the framework for one person to digitally and legally represent another is still maturing.
4: Everyday Commerce: Smart Payments
Having settled into her new life, Lara’s EUDI Wallet now transitions from a tool for foundational life events to a companion for everyday convenience. The final step in her journey for today illustrates a fundamental improvement for e-commerce experiences. She decides to buy a bottle of Italian wine from a local online shop. At checkout, instead of a page of forms, she sees a single, elegant button: "Pay with EUDI Wallet"

Tapping it initiates a powerful, consolidated interaction on her phone. A single screen appears from her wallet, clearly stating that the merchant is requesting two specific pieces of information from her PID: her name for the order and a simple confirmation that she is over 18. The wallet makes it clear that her full date of birth or other personal details will not be shared. Simultaneously, the screen asks her to authorize the payment of €23.58 with her credit card. She approves the entire transaction with a single biometric authentication. She is then automatically redirected back to the online shop, where her order is now confirmed.
This seamless flow is a prime example of data minimization in action, a core principle of the EUDI Wallet's data exchange model. The merchant gets exactly what is required for the transaction and for legal compliance, without accessing unnecessary personal data. This builds user trust. At the same time, the payment approval is a seamless use of the wallet for Strong Customer Authentication (SCA), fulfilling the strict requirements of Europe's payment directives. As outlined in guidelines from payment industry bodies like EMVCo on using the EUDI Wallet in 3-D Secure, this method is set to become a primary way to authorize payments securely.
Furthermore, the experience enhances user control through transparency. In her wallet's activity log as part of the dashboard functionality, Lara can review a complete, chronological history of every interaction—from her initial PID issuance to the bank KYC, credential issuances, and her recent payment. This mandated dashboard provides a transparent, auditable trail of her digital footprint.
Of course. Here is the draft for the next chapter, which begins Part B of our guide. This chapter focuses on the essential preparatory work organizations must undertake before they can offer wallet-based services to users like Lara.
Part B: The Organization's Playbook – Engineering the Experience
Lara’s seamless journey is the result of a carefully engineered back-end infrastructure. For any organization—be it a bank, a insurance, or a government agency—connecting to the EUDI Wallet ecosystem is a significant but manageable undertaking. It requires a technical bridge that can translate an organization's business needs into the secure, standardized language of the wallet framework.
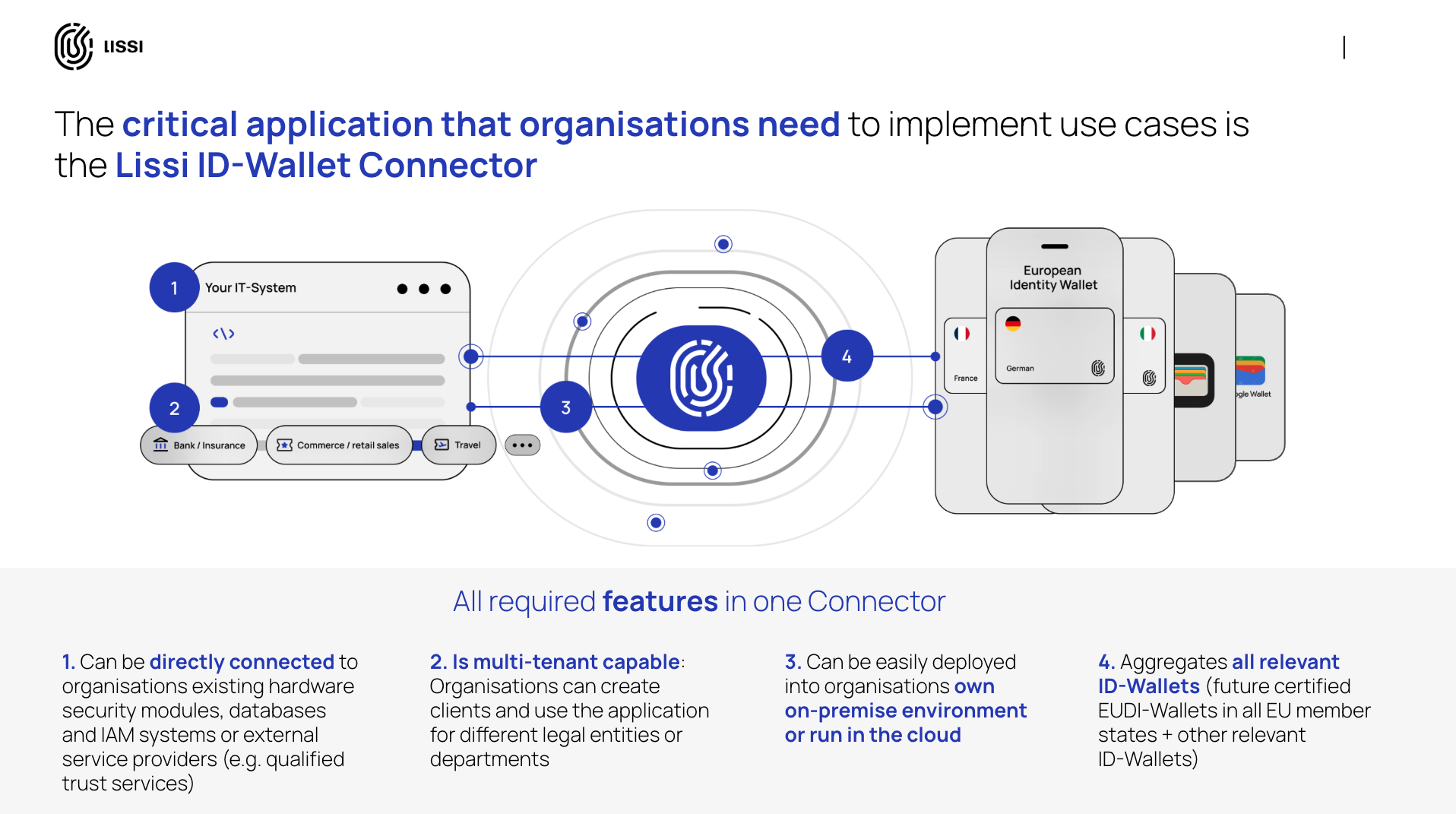
This is where solutions like the Lissi EUDI-Wallet Connector come in, providing the essential API-driven infrastructure. The Lissi Connector guarantees continued compliance with the technical eIDAS requirements as well as interoperability with all certified EUDI Wallets.
This component is designed for organizations that want to host the application in their own cloud environment to implement use cases themselves, as well as for those aiming to act as intermediaries for their own portfolio of customers. The following chapters provide a practical playbook for this process, broken down into two key phases: Use Case Setup and Use Case Execution.
5: The Use Case Setup Process
Before any user interaction can take place, an organization must first formally establish its identity and define the rules of its use case within the EUDI Wallet trust ecosystem. This setup phase is a critical foundation for security and a smooth user experience.
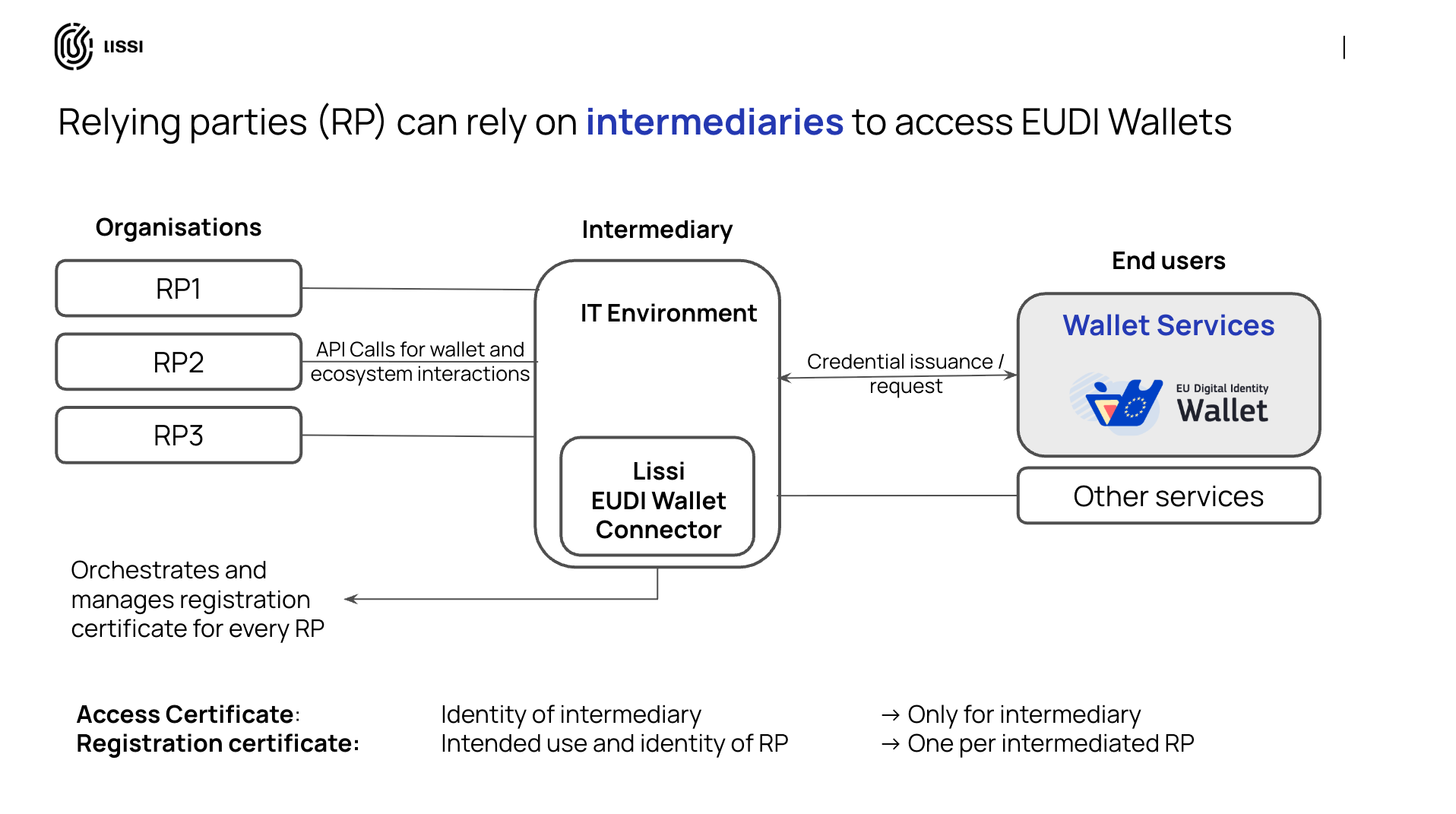
The first mandatory step is Relying Party Registration. As detailed in the Architecture and Reference Framework and legally mandated by the corresponding Implementing Act, every organization that wants to request data from a wallet must be officially registered. This process involves obtaining cryptographic keys and certificates—specifically Access and Registration Certificates—that prove the organization's legal identity and authorize it to operate within the ecosystem.
For organizations, managing this process can be complex. A solution like the Lissi Connector simplifies this by facilitating the creation of a Relying Party registration profile and automating the management of these vital certificates for different use cases. Furthermore, a crucial part of the setup is the configuration of the Relying Party itself. This involves defining the data that will be displayed to the user in their wallet during an interaction, such as the organization's official name, logo, and the explicit purpose of the data request. A clear and professional presentation at this stage is essential for building user trust and maximizing conversion rates.
.png)
Finally, the setup phase culminates in defining the logic of the use case itself through templates. For both issuing and verifying credentials, templates allow an organization to define a specific interaction flow once and then reuse it repeatedly. For a verification, this means specifying precisely which credentials and attributes are required from a user for a given process, like KYC. However, defining a verification request can be a highly complex task. The underlying standards are designed for maximum flexibility, allowing a single request to involve specifying multiple required credentials, restricting them by issuer, and defining granular constraints on specific data fields.
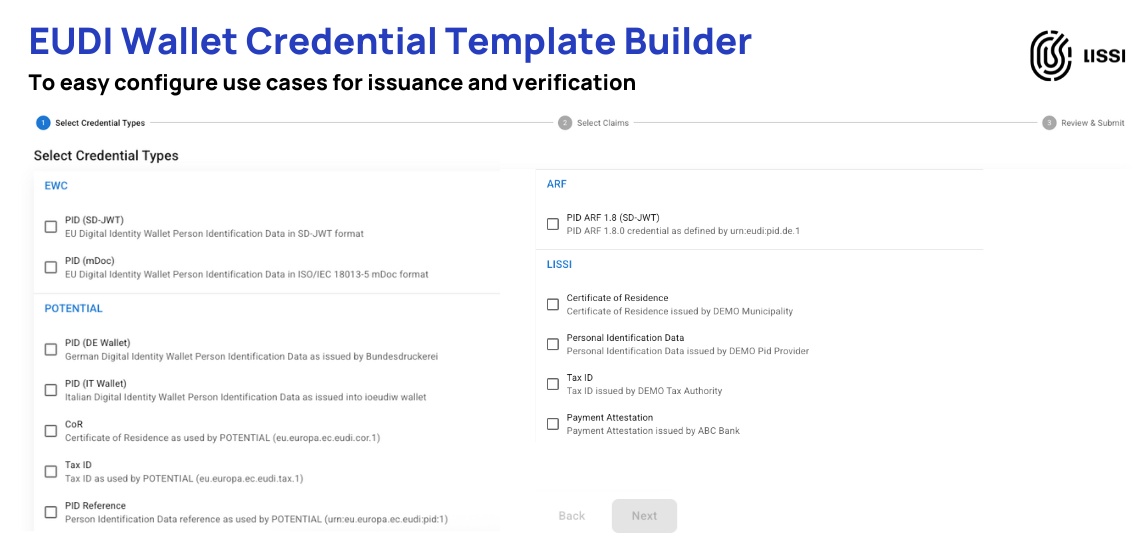
This is configured using protocols like OpenID for Verifiable Presentations (OpenID4VP) and its associated query languages, which require deep technical expertise to implement correctly. Expecting every organization to master this complexity creates a significant barrier to adoption. A solution like the Lissi Connector abstracts this entire layer, translating the complexity into a manageable API. To further simplify this process, Lissi also provides a template builder UI, enabling product managers and business analysts to visually configure and test even complex use cases like SCA or KYC in minutes, dramatically accelerating the time-to-market for new wallet-enabled services.
6: The Use Case Execution
Once the setup is complete, the focus shifts to executing the live interaction. The primary UX challenge at this stage is to manage the transition from your service to the user's wallet and back as smoothly and securely as possible. A broken or confusing flow at this point will lead to high user drop-off, nullifying all the preparatory work.
The standard interaction model is based on a redirect flow, which must intelligently handle two primary scenarios. In a same-device flow, where Lara interacts with your service on her mobile, a "deep link" is used to automatically open her wallet app to handle the request. In a cross-device flow, where she starts on a desktop, your website must generate a QR code for her to scan with her phone. A robust implementation must support both patterns. The key to making this redirect seamless and secure is the use of Callback URLs and proper session handling. The initial request sent to the wallet must contain a unique session ID and a specific URL where the user should be returned after they approve or reject the request. This ensures that when the wallet redirects the user back to your service, your backend can securely match the response to the correct, ongoing session, creating a continuous and trustworthy experience.
While the redirect model is the current standard, the future of wallet integration lies in creating more native, in-app experiences. This is the purpose of the Digital Credential API. Instead of the user's app switching to the wallet and back, this emerging API allows for a more direct and seamless communication channel between the organization's application and the wallet, all happening in the background with the user's explicit consent. For the user, the experience can feel almost magical—they can stay within your application while the necessary credential exchange happens instantly and securely. This approach represents the next frontier of wallet UX, and Lissi's software stack already offers full support for the Digital Credential API. By providing the tools for this advanced integration today, we enable visionary organizations to build the most deeply integrated and user-friendly services of tomorrow.
Part C: The Ecosystem's Responsibility – Building Public UX Infrastructure
Lara’s seamless journey in the previous chapters was made possible by the individual organizations that engineered their services for the EUDI Wallet. However, a truly user-centric experience depends on a set of shared public infrastructures that no single organization can build alone. This is the ecosystem's collective responsibility.
7: The Discovery Challenge: Connecting Users, Issuers, and Services
We join Lara after she has successfully set up her wallet and loaded her official PID. Her wallet is secure, but it's also mostly empty. She knows she is eligible for a host of other digital credentials—her university student ID is just one example, but what about a public transport pass, a library card, or a loyalty card from her favorite retailer? A user cannot be expected to manually hunt through dozens of websites and portals to find out who issues which credential. This "empty wallet" or "cold start" problem is one of the most significant hurdles to mass adoption; a wallet's value is directly proportional to the number of useful credentials it contains.
The solution to this lies in a shared public utility: Issuer and Credential Discovery. This is the "yellow pages" for the digital identity ecosystem. It is a mechanism that allows Lara's wallet to ask foundational questions like, "Which trusted universities in Milan issue a digital student ID?" or "Where can I get a digital proof of my professional license?". This requires a coordinated, trusted infrastructure that wallets can query to present users with a browsable catalog of available credentials. While the eIDAS will deliver a catalogue of attestations, its aim is to standardise which attributes will be part of credential, not where it can be found. Pioneering projects like the Fides Credential Catalog are early examples of this essential infrastructure, which will be vital for organisations to configure use cases and users to easily and securely populate their wallets.
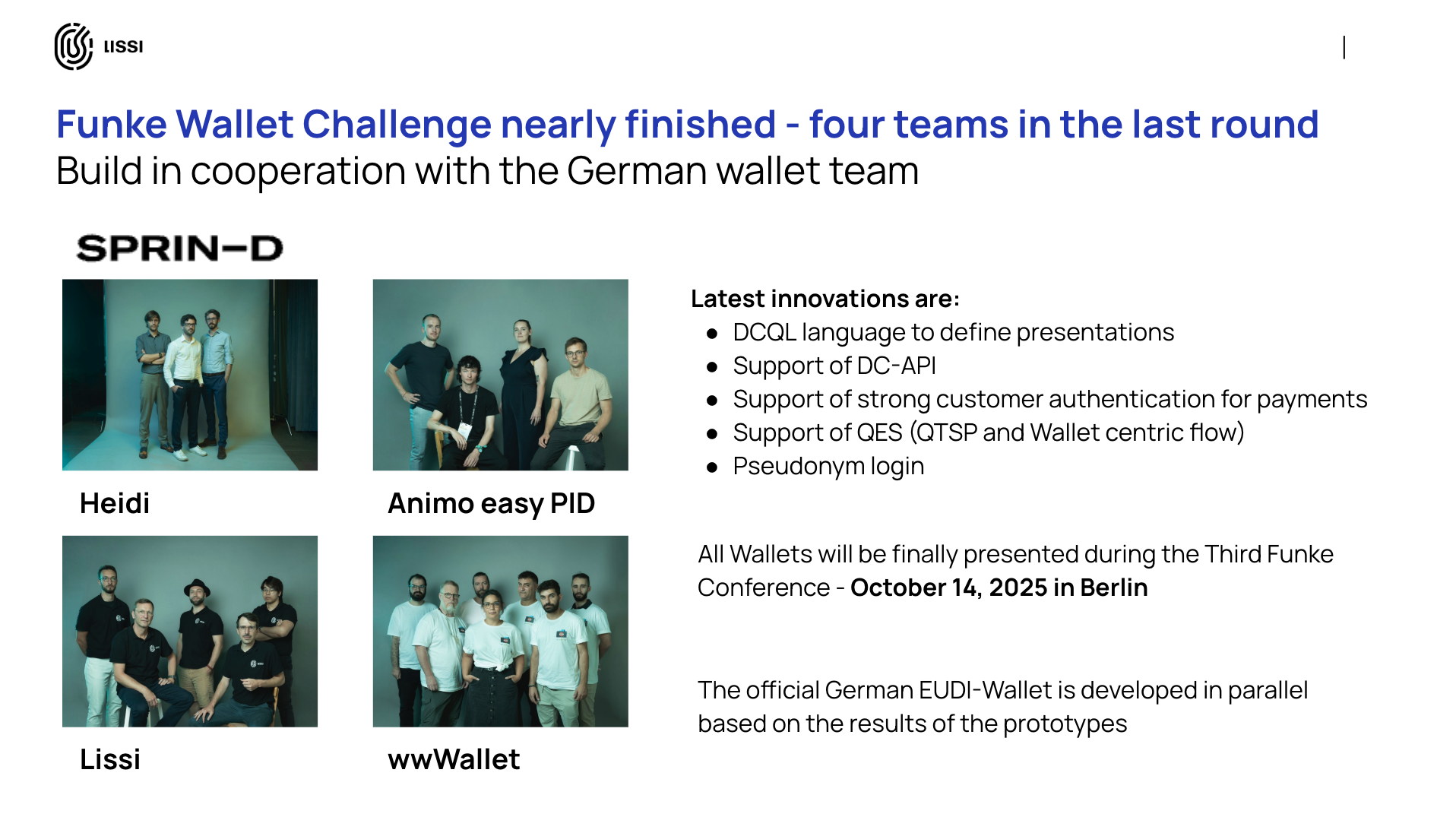
Discovery, however, is a two-sided challenge. Once Lara has credentials, she faces the opposite question: "Where can I use them?" This is the problem of Use Case Discovery. For the wallet to become an indispensable part of daily life, users need an easy way to find services that accept their credentials. Imagine Lara's wallet notifying her of all the local museums that offer student discounts, or a map showing the e-commerce sites that accept her wallet for a seamless, one-click checkout. This functionality is what will drive repeat engagement and transform the wallet from a tool for occasional administrative tasks into a daily companion. Solving this complex discovery challenge is a key focus for innovators in the ecosystem, which is why Lissi, as part of the German SPRIND/Funke wallet challenge, has already designed and implemented a native credential discovery service, demonstrating a practical path forward for this critical UX component.
8: The Work in Progress: Who is Building This Future?
The journey toward a seamless EUDI Wallet experience is not a theoretical exercise; it is being actively built, tested, and refined by a network of collaborative initiatives across Europe. Understanding how these groups are solving today's UX challenges provides a clear picture of the ecosystem's maturation. The work is happening on multiple fronts, from large-scale real-world tests to the foundational work on technical standards.
.png)
The primary proving grounds have been the Large-Scale Pilots (LSPs). The four recently completed pilots EWC, POTENTIAL, DC4EU and NOBID, were instrumental in moving the EUDI Wallet from concept to reality. They generated invaluable feedback by testing use cases with real citizens, and their findings have been crucial in identifying and addressing real-world UX hurdles. This iterative process continues with the two new LSPs We Build and Aptitude set to launch. They will build on these learnings to tackle the next generation of implementation and user experience challenges.
At the technical core, a great user experience relies on robust, interoperable standards. Here, the OpenID Foundation plays a pivotal role. Its work on the OpenID4VC protocol family provides the very foundation for a user-friendly and secure credential exchange process. The importance of this protocol, which was initiated in the German-led IDunion consortium, cannot be overstated, as it governs many of the core interactions that define the wallet's UX. Alongside it, standardization bodies like ETSI are formalizing the technical specifications for trust services and credential formats, ensuring a consistent and reliable experience for all participants.
At a national level, focused initiatives are accelerating innovation. Germany's Funke project, hosted by SPRIND, serves as a high-speed innovation hub where participants like lissi implement and test cutting-edge features ahead of the broader market. Crucially, the insights gained from such projects are shaping the understanding of the need for a national ecosystem orchestrator—a central entity that facilitates trust and interoperability between all participants.
However, this national-level innovation is not limited to Germany. Poland's highly successful mObywatel app, for instance, serves as a model for achieving high user adoption with a wide range of integrated public services. Italy is demonstrating a pragmatic and rapid rollout of its IT Wallet, bringing tangible credentials like the driving license and health card to citizens. Meanwhile, the Netherlands has established a public EDI community platform to foster open discussion and co-creation. These diverse national approaches create a rich pool of practical knowledge that benefits the entire European ecosystem.
Finally, these diverse efforts are being harmonized at the highest level by the eIDAS Cooperation Group. This is the official forum where Member States and the European Commission collaborate to ensure that the learnings from pilots, the work of standards bodies, and the innovations from national projects result in a coherent and truly interoperable pan-European user experience, rather than a fragmented collection of siloed systems.
9: Conclusion: A Call for a Collaborative UX Roadmap
Lara's journey—from her initial wallet setup to her seamless life as a European student and consumer—is a tangible demonstration of the EUDI Wallet's profound promise. It illustrates a future that is not just more efficient, but also more secure, private, and fundamentally more user-centric. As we've seen in the Organization's Playbook, delivering this front-end simplicity is the result of significant back-end engineering and thoughtful design. The tools and standards to build these experiences are no longer theoretical; they are here today, and the transformative potential is being recognized by leaders across the industry, as seen in visionary discussions at major events like the European Identity & Cloud Conference.
However, the vision of a truly seamless pan-European ecosystem is not yet a reality. While individual organizations can and must perfect their own user flows, the greatest remaining UX challenges are systemic. Issues like universal credential discovery, harmonized Relying Party registration, and consistent cross-border interaction patterns cannot be solved by any single company or even a single Member State. They require a coordinated, collaborative effort to build the shared public infrastructure that underpins a great experience for all. To ensure the multi-billion Euro investment in this ecosystem delivers on its promise, we must move forward together.
To that end, we conclude with two concrete demands for the ecosystem's leaders:
- We call for the establishment of a permanent, official, and open forum dedicated to the EUDI Wallet User Experience. The Large-Scale Pilots were a vital first step, but their learnings and feedback loops must not disappear. A continuous, open dialogue between wallet providers, relying parties, standardization bodies, and user representatives is essential for identifying and resolving cross-border UX inconsistencies and for fostering a culture of perpetual improvement.
- We call for the publication of a public UX feature roadmap from the EU and national bodies. Organizations building on the EUDI Wallet need predictability. To make informed investment and development plans, they need to know when critical ecosystem-level features like discovery services, harmonized registration APIs, and new credential formats will become available. A public roadmap is essential for creating a reliable planning horizon and enabling the private sector to innovate in lockstep with the public infrastructure, a key topic of discussion for practical implementation.
The future of digital identity in Europe is not something to be passively awaited; it is something to be actively built. The technology is ready, the vision is clear, and the work is underway. We invite you to experience what is possible today in our interactive Lissi Demo.


.png)
